Let’s talk about Heartbleed for a second, shall we? Perhaps not about the bug itself, but rather about it’s real world ramifications. What does a small implementation mistake mean for an average citizen of the web? Well, probably the most important implication here is that all three of your favorite passwords are now compromised forever. They are all likely on a number of big lists, tied to your email address, real name and god only knows what else. These lists were and still probably are harvested from vulnerable servers, tucked away in some dark corner of the web passed by reference via torrent files. Of course it is entirely possible that your emails and passwords were never harvested and saved for posterity, but are you willing to take that chance?

If you don’t know what Heartbleed is, stop reading this right now and go change ALL your passwords. I’ll wait.
If I was a nefarious individual (or an employee of a clandestine American intelligence agency operating without any public oversight whatsoever) and I was in a possession of a large number of username and password pairs harvested during the bountiful Heartbleed season, I’d continuously run them against various free email services and social networks. After all, why not? There are still many people out there who do not think Heartbleed was a big deal, or that the are somehow immune to it by virtue of not being very tech savvy. There also exist people who have changed their passwords, but will revert back to their old standbys once they judge enough time has passed. And all of these people will likely be owned. The sad truth is that any password you have used while Heartbleed was in effect, is now forfeit forever. You can never, ever use it again. At least not unless you wish to keep that account under your control.
This is how it goes: if I know a password for one of your social networks, games or other bullshit accounts, chances are it is the same one you use for your primary email account. If I know the password for your primary email account, I literally own your life. I can reset any of your other passwords, I can look at your pay stubs, likely log in to your bank account, approve charges on your credit cards, cancel your utilities and etc. Just about everything you do online feeds back to your email, and uses email notifications to warn you about possible fraud, illicit access or misuse of your accounts. That email is protected by a single password and once I know it I can go in and proceed to lock you out of it. This is really bad.
In the real world, when we want to secure something and prevent other people from accessing it, we typically use a key. Assuming that your lock of a good quality and it can’t be easily picked, the benefit of using a key as an authorization/access method is fairly obvious: it is a physical token that is easy to control. You usually only have one or two keys, and they can’t be easily replicated without physically taking them to a locksmith. So as long as you keep your key safe, and don’t give it to anyone, your possessions are as safe (or at least as safe as the lock and safe integrity will allow them to be).

These are physical tokens. They are non-trivial to replicate without physical access. When you lose one, you know almost instantly that it is gone.
We also use combination locks, but they are inherently less secure. Sometimes that’s exactly what you need. For example, if you want a friend to get your textbook from your locker in the hallway you can just tell them your combination. Unfortunately, everyone else within the earshot will also know your combination at that point. This is partially mitigated by the fact that most of combination locks let you change their code. Unfortunately, if you don’t know someone might have overheard your combination, or even seen you enter it, you won’t be compelled to change it. This type of lock gives us the convenience of not having to carry around a key, and to easily grant others access in exchange for lessening of overall security. Instead of relying on a physical token that unlocks the door, you instead use a secret pass-code which can be overheard, guessed or even extracted from you via subterfuge. This is why combination locks age common on high school lockers, or bicycle chains, but your car or your house will typically use a key based lock.

This is a password/secret based security device. The combination can be stolen without you ever knowing. If someone knows the combination they can share it indiscriminately at virtually zero cost.
At the dawn on the internet age, we did not really have an affordable and logistically sound way to model physical keys, so we settled for password based authentication. It is functional, but not a perfect solution as evidenced by the fact people get their accounts “hacked” all the time. The fact that passwords get compromised so often is a feature of their design. They rely on a users doing something we humans were never really good at to begin with: retaining random codes in memory.
With the way our minds evolved, our memory is very referential. We rely on context cues for retrieval and management of our memories. We are good at remembering people, events and emotions and facts that tie into them. Unfortunately that does not help us with passwords, which to be secure must be completely random and devoid of context or emotional content. If your password is based around something or someone who is dear to you, then it will be both easy to remember and easy to guess. If you use words, you leave yourself vulnerable to a brute force dictionary attack. So not only do you need a password that is devoid of context, emotional investment, but also is unpronounceable and a complete gibberish.
If you only needed to remember a single completely random string, this wouldn’t be that bad but we all have dozens of online accounts. Ideally, you should use a unique password for each of them. If you re-use the same password on all the services, then a tiny coding mistake on one of them can potentially leave all of your online accounts wide open. So in an ideal world you would have to remember 20-30 unique random, unpronounceable complex passwords. And all of them should be more than 30 characters long if you want to stay ahead of the curve and make them difficult to crack via rainbow tables. This sort of mnemonic feat is something beyond the capability of any modern man.
This is simply not what we are wired for. And so, most of us have three or four favorite passwords that we re-use all over the internet. The savvier netizens have some sort of stratification in which they use the strongest, most complex password for their primary email / bank account, and then a number of lesser passwords for various other services. Most people however don’t do this, but instead rely on a kind of chronological password system. They have their current password which they use for all the important stuff, their previous password they use on things they could not have been bothered to change and old passwords they no longer really use, save for a few ancient accounts, and maybe as a throw-away password here and there. This is why Heartbleed is so scary. Because of it, all these three or four passwords are now more or less public knowledge and you’d be a fool to use them ever again.
Passwords are broken by design. They simply do not work for what we’re trying to use them. They have been a good compromise up until now, but it is time to move on. If we want even an illusion of security online, we need to start using physical keys again.
When I took an infosec course in college, I remember discussion we had about two factor authentication. It was a very good solution to the password problem. It works by combining a secret (something you know) with a physical token (something you have) and requiring both these elements to be used together at the same time. Knowing someone’s password is useless without also obtaining physical access to their token. Stealing someone’s token is useless without knowing their password. While it does not protect you from a MITM attack, use of a changing/rotating token can limit it’s the scope from permanently compromising the account to merely a temporary breach. It is really a perfect solution… Except it was logistically impossible.
Back then the only reliable way of implementing this scheme was to issue a user a little electronic, battery operated, key-chain token, with a tiny LCD that would display rotating numbers. It was something you did when you were a big technology company with a big security budget to blow: like Microsoft, IBM or Oracle maybe. The expense of creating, issuing, mailing, replacing and managing such devices was so mind-boggling that most banks and credit card companies refused to even consider it. It wouldn’t even be an option for all the fledgeling new free web services that were revolutionizing the way we did business online. It was a beautiful pipe dream: it would be amazing to have two factor auth on everything, too bad it will never, ever happen. And even if it would, how the hell would that even work? Would you even be able to strap 40+ RSA tokens to your car keys? Would men have to think about investing in man-purses or fanny packs to carry all those plastic tokens, cards and dongles? It wasn’t something that was affordable by the web companies or desired by their users.

RSA Tokens have always been and still are an industry standard. They’re good, but they are expensive to maintain, and users constantly lose them, forget them and generally hate to carry them around.
Fast forward to 2014 and we live in a completely different technological landscape. Most of the internet connected human beings who participate in e-commerce already own and always carry around perfect physical, internet-enabled tokens. Hell, they not just carry them – they treasure them. To many, these devices are cherished status symbols. I’m of course talking about cell phones.
An unique property of a cell phone that distinguishes it from other electronic devices is that it can receive phone calls and text messages. Unlike email, the SMS system is tied to a physical device. In most cases it is impossible to read your text messages without physical access to your phone, and any interruption service (due to interception) is likely to be noticed. So if I build a website that challenges you to enter a randomly generated security code after you enter the correct password, and then I text that code to your phone… Well, we just implemented 2 factor authentication for free.

Technically, this is a perfectly valid physical token for SMS based 2-Factor authentication. It’s probably pretty safe to assume that everyone who uses the internet regularly probably also owns a phone just like this, or better.
Actually, scratch that. It’s not free, because sending text messages costs money. Also, implementing a system that can send text messages merely to the few existing cellular networks (all of whom have price-fixing and non-competition agreements with each other but for some reason can’t make their networks work together) in US is already a major pain in the ass. But still, it is a viable option. And a one that has no barrier of entry and can be readily used by just about anyone who can operate a cell phone. Not even a smart phone mind you but a basic, flip phone even. But if you don’t have money or resources to implement and SMS based solution, and you expect your users to be savvier smart phone owners you can do it in software at little to no cost.
All you need is a phone app that implements the HMAC-based OTP Algorithm. Most modern phones (even the Blackberries) have enough processing power to run an app that can reliably generate a random security code every 30 seconds. The Google Authenticator app is only a one example, and there are many other, and they are all cross-compatible. If the user doesn’t like or trust Google they can choose an equivalent solution from one of the dozen other vendors. Implementing the challenge response on the server side for the HMAC-based OTP is so trivial it can be even shipped as a one-click install WordPress plugin.
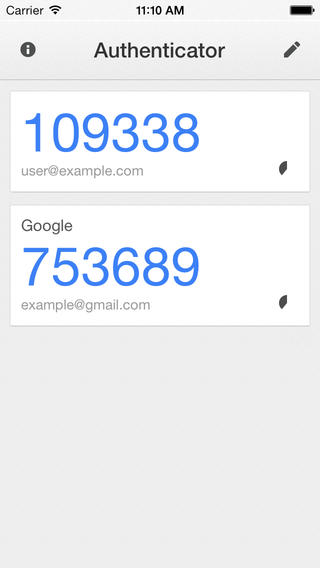
Google Authenticator on iOS. Contrary to popular belief this is not a Gmail Login app, but a full implementation of the HMAC-based OTP algorithm and it will work with any service (including LastPass).
In the age of both the ubiquitous cell phone use, and rampant identity theft, two factor authentication is now so trivial to implement it would almost be foolish not to. To wit, most prominent online services already use it: Facebook, Twitter, Google, Yahoo, Microsoft, Tumblr. You name it. Most of these offer an option to use SMS and software based solution. All are disabled by default, but can be enabled at any time. And in the aftermath of Heartbleed it would be foolish not to use it.
Few months ago you could have made a compelling case why you might not need two factor authentication on your email, and I might have believed you. But then we’ve seen a live proof that a simple coding slip-up can compromise half of the internet in the blink of an eye, and that point is no longer valid. You need two factor authentication on everything you can. That is the only way to give yourself at least a fleeting chance against the next bug of this magnitude. It is also the only way to prevent someone from extrapolating your next password based on your last seven previous ones, which, as we established, must be assumed to be public knowledge now.
You’d be astonished to see just how many online services already implement 2-Factor Auth. You’ll probably be doubly astonished that almost none of them are financial institutions or banks. So while you may not be able to make the place which holds your money to be more secure, you can make sure that at the very least your email (which is the gateway to your bank anyway) is. So I implore you to at least consider it.
Now, if you want to maximize your security, this is probably what you should do:
- Sign up for a password manager such as LastPass or 1Password
- Use the password manager to generate 30+ character long, completely random passwords for everything.
- Secure the password manager with a 30+ character pass-phrase you can remember.
- Enable 2-FactorAuth for your password manager (possible for LastPass at least)
- Enable 2-Factor auth on all the services that support it, on the off chance that they get man-in-the-middled or in case your password manager is compromised.
This of course won’t make you 100% safe. Nothing ever really will. But it will ensure your identity is a little harder to steal. And that’s actually a good defense mechanism. Effort is the anathema to a black hat. Hacking is a low effort high profit kind of game, and it is much easier to move to the next guy who thinks he is invulnerable to Heartbleed than tackle someone who had enough foresight to click a button 3 times to enable 2 factor authentication.
Just wanting to point out that there is also a WordPress 2factor authentication plugin… but you are not using it ;)
Actually, I am. :) It only triggers after you log in with valid username and password though, so I’m pretty much the only person who sees the 2nd step which is actually perfectly find by me.
My problem with SMS-based 2FA is that it’s tied to a device I carry with me which can be easily lost or stolen. If I lose my phone, or it gets stolen, and my provider decides to screw me around about switching my number to a new SIM (it wouldn’t be the first time), I’ve lost access to my accounts. That said, looking at that list you linked, I didn’t realise software 2FA was quite so prevalent, so I may have to go through my accounts again and see what’s available… and possibly compromise on my backup and password policy of “I should be able to flee the country with nothing but the clothes on my back without losing more than an hour’s worth of data” for any important sites that only offer SMS-based 2FA.
The only problem I see with 2 factor identification is that, I am super paranoid of losing my phone, I would then be locked out out of many many accounts.
Ah Luke, you are to real-world locks as most of the “tech clueless” are to Heartbleed-style security issues if you think anyone outside of large corporations and government agencies are using locks that are difficult to pick. ;)
Liudvikas wrote:
Each account setup probably involves being shown a barcode. Keep a screenshot tucked away in an encrypted volume.
@ Liudvikas:
Most of the SMS based services will prompt you to print-out or save a set of “panic codes” or “recovery codes” which are one time passwords you can use in lieu of the 2nd factor in case you lose the activated device. So you have to lose two things to get completely locked out.
Also, Facebook, Twitter and etc let you designate some computers as “trusted” machines and bypass the 2nd factor when you log in from them. The logic is that you probably want the 2nd factor on unknown machines and maybe on your work laptop, but perhaps not on the desktop in your bedroom. So chances are that even if you lose the phone, you can still get in and disable it from some of your machines.
@ Jason *StDoodle* Wood:
While it’s true that most of general purpose locks are trivial to open using a bump key, I was thinking more alongside design principles. Keys are designed to be secure unique tokens, whereas combinations/passwords are designed to be easily exchanged.
@ Matt`:
This is true for all the HMAC-OTP systems. The SMS based systems don’t use QR-Codes but instead ask you to give them your mobile phone number so they can text you the codes.
@ Luke Maciak:
Ok I am convinced, any advice which option is best for lastpass?
@ Liudvikas:
Personally I use Google Authenticator because it is a standard HMAC based OTP implementation. It works for me because several other services I use (including Linode and Digital Ocean web panels) use it as a primary 2Factor tool.
Youbikey is interesting because it is not phone based but a real physical token. This means it’s easier to lose, and it may not be easy to ship overseas. Also, when I looked into it was basically a thumb-drive with an encrypted partition, and some binaries that were auto-run when you plugged in… And it had no support for Linux which was a deal-breaker for me.
Duo and Transakt seem more intuitive for end users, but they seem to require some communication with their servers. Their authorization seems to involve the site pinging their servers to push an acknowledgment notification to your phone, you acknowledging the login via app, which gets sent to their server and back to the site which initiated the challenge. That seems like too many moving parts. Also I have no clue what happens if their servers go down, or are blocked by a firewall.
Google Authenticator churns numbers locally, so it will work even if Google stops supporting it. Also it’s a standardized algorithm so you can replace the authenticator app at any time.
Oh, and you can screen-shot the QR-Code as backup to re-authenticate with a new device if needed – which as far as I can tell is not an option with the other methods. So in my mind it is clearly superior.
Man, if I had know you were this helpful in the comments I would have asked for protips about how to accomplish automatic back ups in your last rant on the subject. Thanks for the clue in about 2FA on so many services outside of gmail.
Pingback: Dear Passwords, I F***ing Hate You | bloomfield knoble
