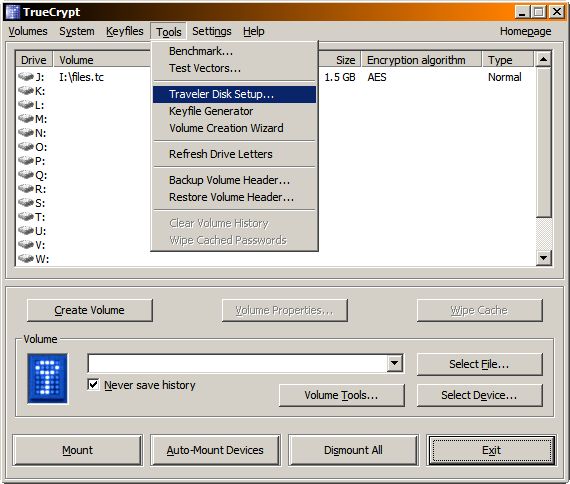
I discovered a neat TrueCrypt trick the other day while searching for products that would encrypt flash drives on the fly. I never noticed it before but it has an option to create a “travel disk”. It’s right there in the tools menu, as you can see on the screen shot below:
It will essentially turn your chosen external drive into a self contained vehicle for TrueCrypt encrypted volume. It will copy all the files necessary for encrypting/decrypting the volume to the drive, and set it up to use the windows auto-play feature. So you just plug it in, type in your password and can start working with the encrypted files. The process is amazingly simple – so easy even a Caveman can do it. ;) You just pick the drive, and choose whether or not it should auto-mount a volume on startup (yes it should):
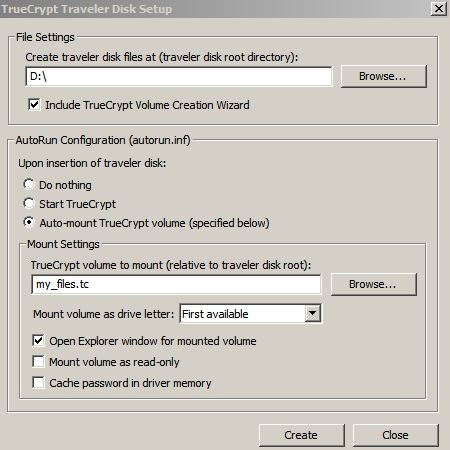
Then you click create. That’s all you really need to do. One thing this process doesn’t do is actually creating the TrueCrypt volume file on that drive. You have to do hat separately – I wrote about how to do this earlier. I created mine ahead of time called it files.tc and plopped it in the root directory of my flash drive. All I had to do then, was to point the above dialog at it. If you don’t have a tc volume yet, you can just type in a file name in that box, – it won’t complain that it doesn’t exist. You can add the volume later.
Once you hit create, bunch of files will get copied to the selected drive:
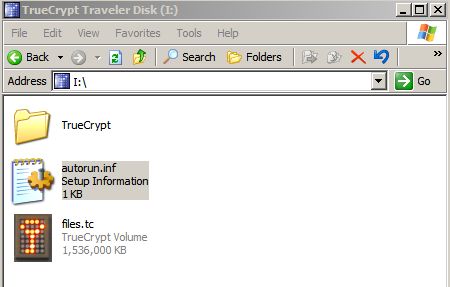
The autoruns.inf is the interesting one. As most of you know, this file contains the commands used by the Windows auto-play functionality. This is what it really contains:
[autorun]
label=TrueCrypt Traveler Disk
icon=TrueCrypt\TrueCrypt.exe
action=Mount TrueCrypt volume
open=TrueCrypt\TrueCrypt.exe /q background /e /m rm /v "files.tc"
shell\start=Start TrueCrypt
shell\start\command=TrueCrypt\TrueCrypt.exe
shell\dismount=Dismount all TrueCrypt volumes
shell\dismount\command=TrueCrypt\TrueCrypt.exe /q /d
In fact this is the only place which references the file name you entered in that dialog box. You can easily change it to anything else and it will work. Inside the TrueCrypt folder you get the guts of TrueCrypt. These few binary files are what does the encrypting/decrypting in the background:

I can give this flash drive to anyone in the world, and as long as they are running Windows XP (I don’t think 2k autoruns flash drives) they will be able to work with it. All you do, is just plug it in, and you see this dialog:
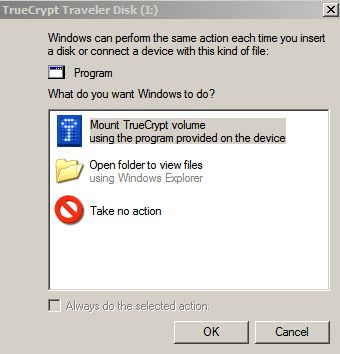
If you choose the TrueCrypt option you will be greeted by the familiar (well, familliar to me) TrueCrypt password dialog:
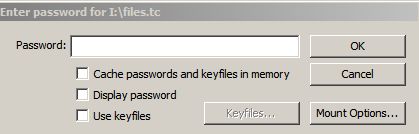
If you give the correct password it will mount another drive on your system, which will be the encrypted volume:
The two drive thing may be confusing to some lusers at first but it opens up the correct one automatically in explorer on startup. Besides, they can easily identify that one drive has some cryptic system files, while the other has their data.
From there it just works seamlessly as always – anything you move, copy to or create on the virtual drive will be encrypted. What encryption will be used? It is up to you. The encryption type is not tied to your copy of portable TC but to the volume you created. If I remember correctly I used 128 bit AES-Twofish combo on mine, but you can pick your own.
The nice part about this is that I can easily take another tc volume (different encryption algorithm, different password) stick it on my flash drive, name it files.tc (or modify the autoruns.inf with the new file name) and it will work just as well. Or I can copy the TrueCrypt folder and the autoruns.inf file to another drive, and it will work as well. I can essentially create a script that will crank these out at will, without even having TrueCrypt copy installed.
I’m considering making this mandatory for the folks at work. They do get a lot of use out of the flash drives – and the do handle confidential stuff sometimes. So this seems like a perfect solution. The only caveat is removing the flash drive from your system.The standard Windows “Safely Remove” dialog won’t work because the .tc file as well as the TrueCrypt binary will be in use. So removing the stick is really a 2 step process:
- Right Click on the TrueCrypt icon in the taskbar and choose “Dismount all Encrypted Volumes”
- Remove the Flash Drive using the usual method
The “Dismount Command” actually shuts down TrueCrypt which is nice. Otherwise it would be a 3 step process. I’m sure that most people in the world can deal with a single manual step when they are getting high grade encryption for free. But my users are not most people – they are the people who will cry about it. But there is not much that can be done about this other than just removing the drive without actually making sure the write buffers are flushed into the thing. I’m concerned that when working with a TrueCrypt volume, pulling out the flash drive prematurely my be doubly hazardous than usual – I have no clue how these encrypted file handle corruption and unexpected write errors.
So I suspect I will have to do a 2 hour phone in training session on this, write up a manual with step by step screnshots (hey, I already have most of them here – nice) and then just be prepared to field phone calls asking how to dismount the damn thing for the next 7 months.
[tags]true crypt, encryption, travel disk, crypt, cryptology[/tags]
The link to the TrueCrypt website in the first paragraph is broken :(
Otherwise, nice how-to – I’ll try it out on my stick :)
Thanks! I fixed it.
i wonder if this could somehow protect the usb drive from usb viruses.
No, it won’t. Part of the drive is still unencrypted and thus can carry a virus.
Format the drive with ext3 or some other linux file system – you shouldn’t get any viruses then :mrgreen:
Yes, because it will be unusable in Windows. :mrgreen:
Unless you install Ex2 IFS. But then I think you can still get infected. :P
yeah, ext3 might do, but you’d need an ext3 fs reader program in your windows before it can be read, right?
maybe i’m just trying my luck to find a lightweight “file manager” compiled statically for windows, and that could be stored in the USB and set to run during autorun.inf in which probably will mount and decode the encrypted drive or read and write to ext3 ;)
That seems like way to much work. And I think that to write/read ext3 you need something at the kernel level (I mean it’s a file system) so a mobile app probably won’t do any good.
Also, if you can write to the USB then the virus can write to it too. I don’t think there is a foolproof way of protecting yourself against these things other than not sticking the flash drive into a potentially compromised machine.
Btw, I don’t think I ever even saw a USB drive based virus in the wild? Is this an actual concern (ie. somewhere where you often go has rampart flash drive viri) or is this just a precautionary thing?
yeah, here in the philippines its rampant, or atleast in the southern part, some local douche wrote it. he had his graffiti on the script as i can see it in my ubuntu, then I get to clean my younger brothers USB drive and also the USB drives of his dozen friends and schoolmates.
it has already spread widely, that any net cafes and computer shops in the region, had this type of virus :(
so anyway, as i was saying maybe theres an foss lightweight filemanager that can be compiled statically , and that has a truecrypt extension and decode it on the fly.. heheh, wishful thinking :)
Why would the way the files are stored on disk affect the way the Windows operating system uses them? I may be missing something fundamental, but I don’t see how the file is stored as having any affect on how it’s used – if Windows can read it and run it, then Windows can be infected by it.
hrm… I may be missing that by using ext3 it’s implied that you’re using linux instead… but you can get ext3 drivers for Windows.
I think Fr3d’s point was that if you format it as ext3 Windows won’t be able to access it without special drivers – and thus no threat of getting infected. Of course you also won’t be able to access your files on a susceptible windows machine :P
Also I linked to the windows ext3 driver above – once you install it, you can get infected normally. ;)
I think his point was, that if you use an ext3 file system and only the static file manager can access it, the virus can’t get in the container. but problem is, either the file manager has to be installed on the machine you use the stick (while the file manager could get infected as well), or you put it in the unencrypted part of the volume and write-protect it.
The only solution would be file manager on unencrypted part, which is somehow write protected (would probably have to be hardware based). then you would lose easy operation via windows drag & drop, but theres no direct access to volume (without file manager) and so no way for the virus.
Please note the reason for Disk Encryption (Note, not file encryption which is different), either on harddisk or on external USB based drives is to proctect the data if lost or stolen (This is what the industry calls Data Secured At Rest). As soon as a drive is opened up the data is available to the end user and any potential virus attacks. To make sure data is not attacked when the drive is decrypted (opened) is to make sure the files themself are encrypted as well, individually.
Basically, use the drive encryption to protect the complete drive and then encrypt required files that requires further protection.
Experience the write protection problem?
As you describe above, unmounting TC files by removing the stick causes trouble. I got some. Vista chrashed, the container was dismounted and .. is now perfectly write protected.
It seems to be no fuqqing way to get the write protection flag off the volume.
I tried to change attributes (write protection = off .. and so on). I also changed the access rights to ensure anybody could change anything. Just to avoid any kind of a problem setting the write protection = off.
So did anybody experience the same problem with a perfectly write protected volume and knows how to remove it?
THX for reading this :)
Unless I’m being dim, it looks like this method requires a TC volume on the portable disk, rather than being able to automagically mount a disk which has been completely TC’d. Best practice might mean have an encrypted & an unencrypted volume on the portable disk then?
@Rich: Yeah, that’s precisely what it is. Only it’s not a TC volume but a TC encrypted file.
It works like this – your disk in unencrypted and it contains two things:
1. an encrypted data file that fills 98-99% of the space on the drive
2. TC binaries + autorun config files
When you plug it in, Windows will mount it pop up the usual message asking you what you want to do – you know, open in explorer, import images, etc… Only because of the autorun file, the top option is now “Mount TrueCrypt Volume”.
You hit that and it runs the TC binary (included on the drive) which mounts the encrypted file as a regular volume on your system.
Yes, from best practices standpoint it would probably be better to encrypt the whole drive. But then it would be impossible to mount it without TC already installed. This way you take TC with you wherever you go and you can use your encrypted media on any computer.
Also, this is actually the preferred method of doing USB media encryption in the industry. We use expensive commercial PointSec disk encryption software at work and it does the same exact thing. It puts some binaries and an encrypted file on the drive.